Onboarding & Integration Journey
In-depth guidance on the onboarding procedures and technical integration lifecycle
Purpose
This guide outlines the complete lifecycle of a client’s onboarding process for API integration — from initial access requests to production go-live and support. It ensures a seamless collaboration between business, technical teams, and the client throughout all stages of API integration.
API Integration Phases
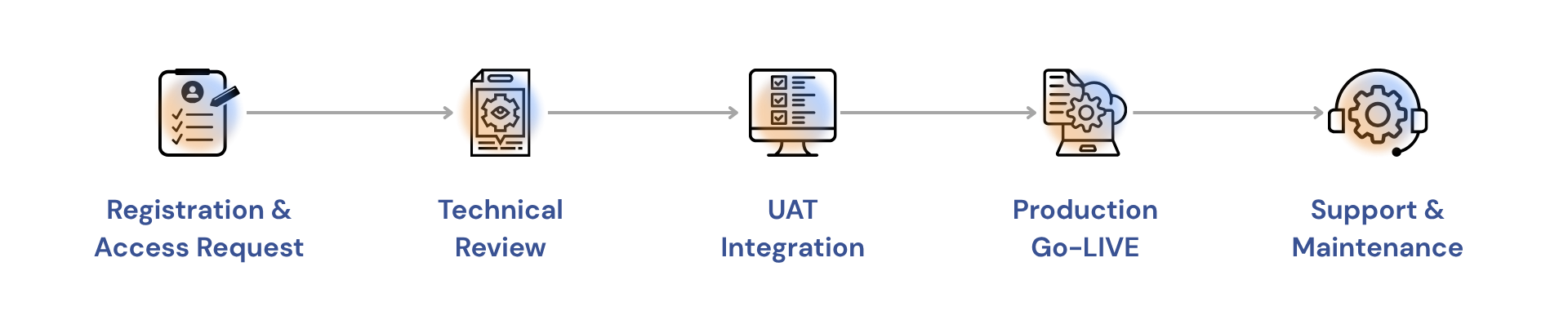
Representation of phases involved during the integration journey for SingleView APIs
1. Client Access Request
Initiation:
- The onboarding begins when the client sends a request for API access via email to the business team.
Required Client Information:
- Anticipated API consumption (e.g., request volume)
- Specific APIs or endpoints of interest
- Use case or integration goals
Outcome:
- Business team collects and verifies initial client information before passing to the technical team.
2. Technical Evaluation & Certificate Validation
Certificate Review:
- The technical team performs a comprehensive check on client-provided certificates:
- Confirms if the certificate uses RSA algorithm
- Validates key size - 2048 bits
- Checks whether the certificate is CA-signed or self-signed
- Reviews the certificate bundle to identify which certificate will be used for signing
Security Assessment:
- Ensures support for mutual TLS (mTLS) using the client’s CSR and CA-signed certificate
- Clarifies with the client which certificate should be configured on the platform
Optional:
- A kickoff call may be scheduled to walk through integration steps and clarify technical requirements.
3. API Provisioning & Documentation
Credential Creation:
- Technical team issues:
Client IDClient Secret
Environment Access:
- Client is subscribed to the UAT (sandbox) API environment.
API Documentation Shared:
- Authentication mechanisms
- Request/response formats and schema definitions
- Header and query parameters
- Example API calls and error scenarios
- Access to:
- Sandbox URL
- Developer guide
- Error codes reference
4. Client Integration & Testing
Integration Begins:
- The client starts developing against the sandbox environment using the provided credentials.
Tech Support Provided For:
- Troubleshooting API errors and integration issues
- Debugging common errors:
400 Bad Request: Usually due to mismatched CSR and certificateMW-401 Unauthorized: Often caused by invalid signature or expired token
- Validating private key and certificate alignment
- Sharing additional request/response samples if needed
Outcome:
- Smooth UAT completion and successful handshake validation
5. Final Testing & Production Go-Live
Production Preparation:
- Upon UAT approval, client submits:
- Production CSR
- CA-signed certificate
Additional Steps (if applicable):
- For APIs that involve bank-side operations (e.g., IBAN Verification), parallel business-bank coordination for legal approvals and agreements is initiated.
Environment Setup:
- Technical team coordinates with banking counterparties to:
- Exchange and validate bank-signed certificates
- Configure and test Mule-to-Bank secure communication
Production Launch:
- Production credentials are generated
- Final confirmation of certificate deployment and API readiness
- Client is subscribed to the production environment
6. Go-Live, Monitoring & Ongoing Support
Client Go-Live:
- API is now live and active in production
Monitoring & Support:
- Real-time API performance monitoring
- Error tracking and response time logging
- Availability and uptime assurance
Continuous Improvement:
- Ongoing collaboration between business and technical teams to:
- Gather feedback from client usage
- Identify enhancement opportunities
- Resolve Post-Live issues promptly
Additional Notes
- Ensure all CSR files are created correctly and keys are securely stored by the client.
- The client is responsible for keeping credentials and certificates confidential.
- Any changes to endpoints or authentication methods will be communicated through official release notes or notices.
Updated 20 days ago